With the explosion of connected devices and corresponding growth in hacks and malware, your business data needs a layered security approach. For QuEST Global, security is a vital aspect across all the projects that it undertakes. We work with clients across a wide spectrum of domains including device manufacturing, defence, automotive, banking and education. Over the years, QuEST has pioneered in implementing security solutions from device to cloud. This is evident from the fact that we have been one of the global R&D partners for Samsung KNOX, played a key role in designing secure ultra-rugged devices for Sonim Technologies, deployed managed security for mobile devices for defense, enabled single sign-on (SSO), Rights Management System (RMS) on top of Microsoft stack, and many more to name.
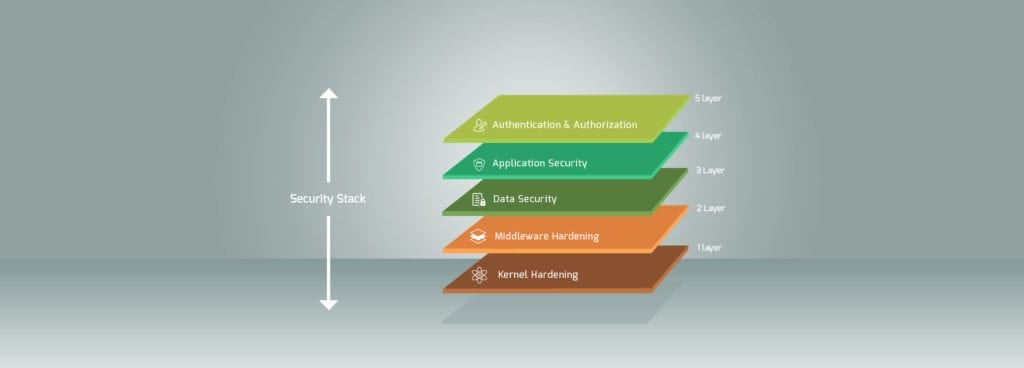
QuEST has the capability to secure devices across various form factors by leveraging the building blocks of security:
TrustZone enabled chipset
ARM TrustZone firmware
Trusted Execution environment OS
Client applications
Securing data-at-rest and in-transit requires comprehensive implementation of security provisions in place. QuEST helps its customers achieve data security through robust implementations such as:
FIPS Certification Services
DRM Services
White Box Cryptography
Rights Management Services
Code security ensures that the solution is robust in all environments. It is extremely important to know not only what the user is doing but also who the user is and whether the user is allowed to do that. That is why authentication & authorization is so important. QuEST has extensive experience in protecting user’s private data by implementing various authentication & authorization protocols. Some of them are as follows:
SAML / OAUth identity management service
Single Sign On
PKI Infrastructure
2nd factor authentication
Certificate & compliance ensures adherence to minimum security requirements for cryptographic modules in products and systems. X` is to promote compliance and ethics through the certification and QuEST has implemented following certifications for various customers:
Some of the certifications that
With the ever present security threats, it is extremely important to ensure that the product or solution can withstand it. One must test their service to make sure that is it secure. QuEST designs security into its customer’s service during the discovery phase and then tests continuously as we build, not as a one-off check. We perform a plethora of tests to endure the solution is secure. Some of the key tests are as follows:
